4-3 Using MCP in Cursor
May 12, 2025
This article is part of our comprehensive Cursor workflow series for engineers.
In our previous article, we introduced what MCP is and why it matters. Now let's explore how to actually use it in Cursor.
Understanding MCP Architecture
MCP follows a client-server pattern that might remind you of how web applications work. Here's the official architecture diagram from the Model Context Protocol website:
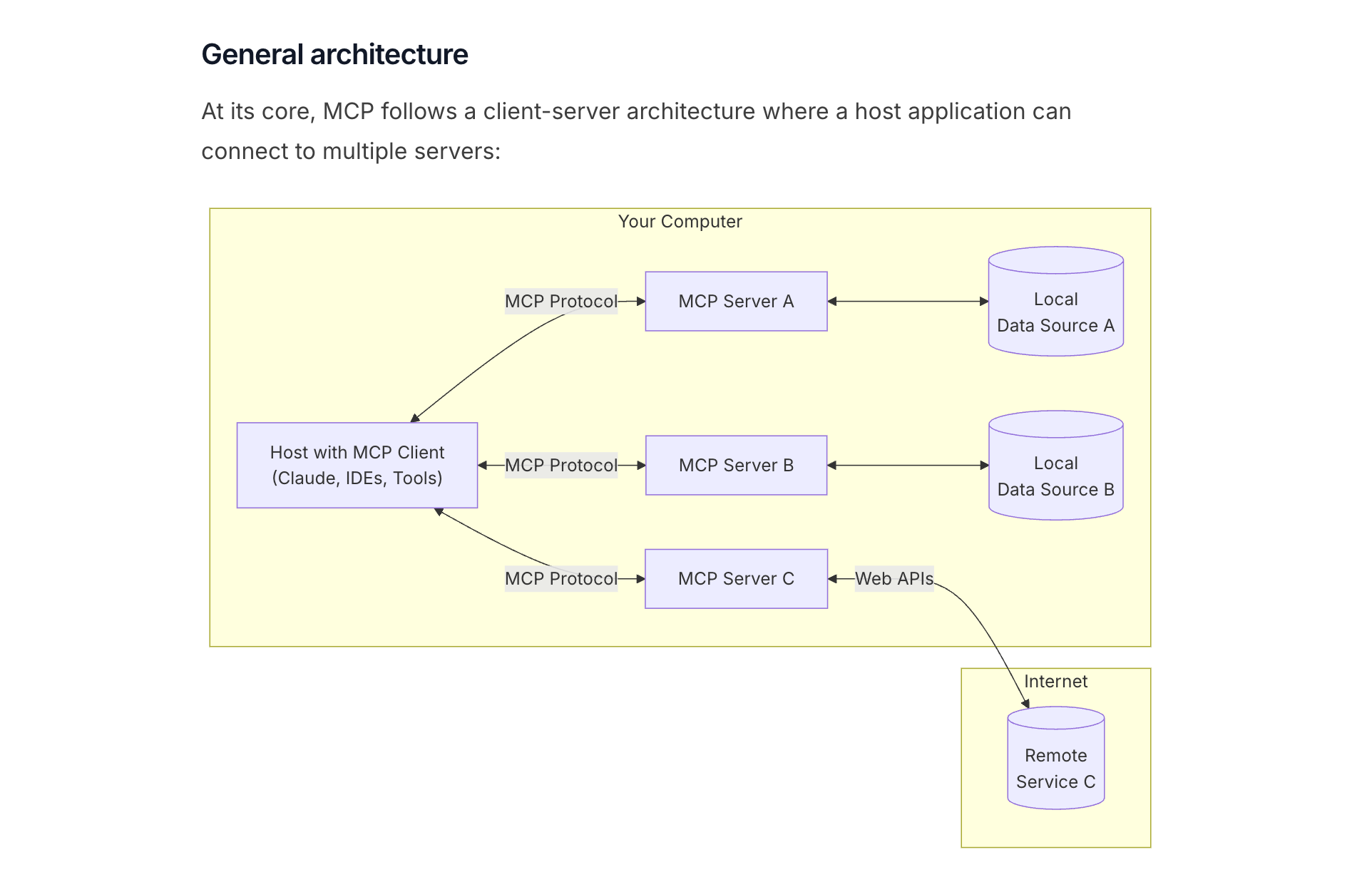
In this setup, Cursor acts as the host that runs multiple MCP clients. Each MCP client connects to an MCP server using the MCP protocol. Behind each server, there's a specific data source or web API—like GitHub's API, Google Drive's API, or Slack's API.
For example, when you use the GitHub MCP server, your request flows like this:
- You ask Cursor's AI to create a GitHub issue
- Cursor's MCP client sends the request to the GitHub MCP server
- The GitHub MCP server calls GitHub's web API
- The result comes back through the same path
This architecture lets your AI agent work with external services while keeping everything secure and manageable.
Types of MCP Servers
MCP servers come in two main flavors:
Local servers run on your machine and connect via stdio (standard input/output). You start them locally, and Cursor's MCP client connects to them directly.
Remote servers are already deployed somewhere on the internet. Your Cursor client connects to them over HTTP. These are more convenient because you don't need to set up anything locally.
The main difference: local servers give you more control but require setup, while remote servers are ready to use but depend on external services.
Finding MCP Servers
You could build your own MCP server (we'll cover this in later articles), but many servers already exist for popular tools.
The official MCP servers repository lists servers for GitHub, Google Drive, Slack, and other common tools. These are maintained by the MCP team and third-party developers.
Community sites like cursor.directory also catalog MCP servers created by developers worldwide.
Security Considerations
Here's an important warning: not all MCP servers are trustworthy. Since these servers can execute code and access external services, malicious servers could potentially harm your system or steal data.
Before using any MCP server, especially from third-party sources:
- Check the source code if it's available
- Read reviews and community feedback
- Start with well-known, maintained servers
- Be cautious with servers that request broad permissions
We'll dive deeper into MCP security practices in article 4-7, but the key principle is: treat MCP servers like any other software you install—verify before you trust.
Setting Up MCP in Cursor
The actual process of connecting MCP servers to Cursor involves configuration files and setup steps that are easier to demonstrate than describe. The specific steps depend on whether you're using a local or remote server, and each server type has its own configuration requirements.
For detailed setup instructions and live demonstrations, check out Cursor's official document (link)
In upcoming articles, we'll explore specific use cases, security best practices, and how to build your own MCP servers for custom integrations.
Support ExplainThis
If you found this content valuable, please consider supporting our work with a one-time donation of whatever amount feels right to you through this Buy Me a Coffee page.
Creating in-depth technical content takes significant time. Your support helps us continue producing high-quality educational content accessible to everyone.
